One of the notorious Russian hackers who has allegedly been raiding American corporate systems for credit card data and other valuable information has been apprehended in Amsterdam and extradited to the United States to face justice.
Taking Vladimir Drinkman down was a massive international operation requiring years of effort. He is a very big fish; the Justice Department describes his operation as “the largest international hacking and data breach scheme ever prosecuted,” and his arrest could be a hopeful sign that international cooperation between cyber-security teams can make life difficult for thieves who assume they are safe as long as they attack American systems from foreign soil.
Drinkman faces up to 30 years in prison if found guilty.
The Washington Post narrates the tense moments leading up to Drinkman’s capture:
At noon on June 28, 2012, Vladimir Drinkman, targeted as one of America’s most wanted cybercriminals, and his wife hustled into a cab pulling away from their Amsterdam hotel. They had just been tipped off that the police were on to them, but an unmarked police car blocked their getaway. The Russian was handcuffed and arrested on charges of helping to mastermind what has been called the largest criminal hacking scheme ever prosecuted in the United States.
This week, after a protracted extradition proceeding, a Dutch court ruled that Drinkman will be sent to the United States to stand trial.
USA Today has a longer list of Drinkman’s alleged targets:
The cyber criminals allegedly struck J.C. Penney, Hannaford, Heartland Payment Systems, Wet Seal, Commidea, Dexia, JetBlue, Dow Jones, Euronet, Visa Jordan, Global Payment, Diners Singapore, French retail chain Carrefour, and Ingenicard, in addition to 7-Eleven and NASDAQ, the indictment said. The indictment accuses the hackers of stealing user names, passwords, means of identification, and credit and debit card numbers.
The gang’s methodology involved gaining access to protected systems with viral programs, which lurked in some of the targeted systems for over a year before cyber-security teams discovered it. The identity thieves would extract valuable personal data from penetrated systems, stash it on computers scattered around the world, and sell credit card numbers on the black market for $10 a pop. USA Today reports they even offered discounts for bulk purchases.
Forbes reports on four other alleged members of the gang whom law enforcement previously identified, with only one of them in custody, although they have been on the police radar screen since 2005: three Russians, Alexandr Kalinin, 28, Dmitriy Smilianets, 31, and Roman Kotov, 33; and one Ukrainian, Mikhail Rytikov, 27.
The gang reportedly communicated with each from their disparate locations using encrypted chat systems, some of which law enforcement evidently penetrated, as Forbes reprints some chat conversations in which they laugh it up about the futile efforts of police and corporate cyber-security to halt their activities. Much of the early evidence for the investigation came from the 2004 Secret Service takedown of a black-market forum called DumpsMarket, where Drinkman is alleged to have posted under the alias “Scorpo.”
Some members of the gang proved far more elusive than others; Similianets was allegedly part of a competitive online gaming team and had 14,000 followers on his Twitter account. The Washington Post has a detailed account of how the operation worked, with one investigator comparing their carefully coordinated division of highly specialized labor to the casino-heist film Ocean’s Eleven. Working under the new alias “Anexx,” Drinkman was allegedly tasked with getting deeper into corporate computer networks after his colleagues made the initial penetration, seeding the network with malware and scooping up valuable data for sale on the black market.
Drinkman is being held without bail for a trial set to begin on April 27; he faces up to 70 years in prison. Naturally, his lawyers are asserting his innocence and playing sympathy cards left and right, as captured in a quote from USA Today:
Over the coming weeks and months, he will finally be able to receive and confront what the government claims is the evidence against him. But most of all, Mr. Drinkman seeks to return to his home in Russia as soon as possible, so his 3-year-old daughter will not grow up without knowing her father.
Attorney Bart Stapert is further quoted by The Washington Post claiming that the U.S. government is basically trying to pin every Russian hacking crime on Drinkman, without “specific evidence” tying him to the laundry list of attacks. Secret Service agent Ari Baranoff countered that his agency has a 99.6% conviction rate for cyber-crime.
Among other crucial evidence, prosecutors claim they have records of Drinkman admitting in a 2012 interview that he was “Anexx.” That sounds like game, set, and match if it holds up, and it could lead to a tectonic shift in the cyber-crime landscape, as foreign hackers are sent an unmistakable message that the days of raiding U.S. networks with impunity are ending.
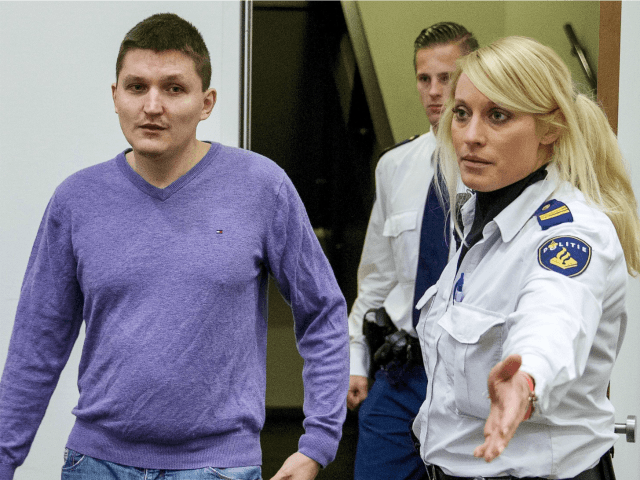
COMMENTS
Please let us know if you're having issues with commenting.