Using a tool likely stolen from the United States intelligence community, hackers launched a massive cyberattack across the world on Friday, hitting government agencies and other organizations in up to 75 countries. The attack most specifically caused havoc in Britain’s health care system.
Early on Friday, Britain’s National Health Service (NHS) was hit by an unprecedented, large-scale cyber attack, sending the agency scrambling to care for patients. The attack prevented care, and disrupted electronic records-keeping across the country.
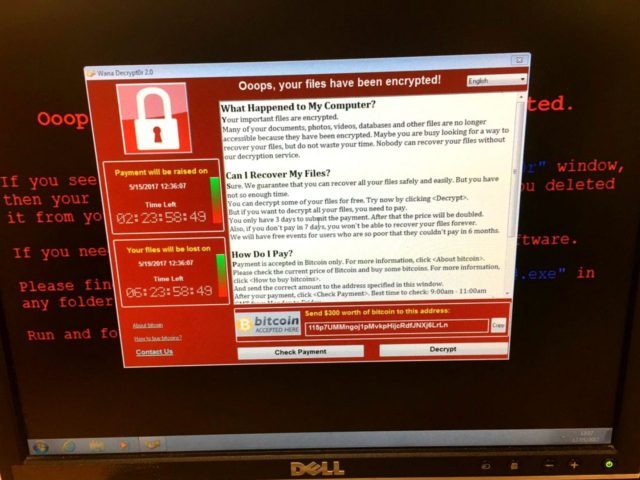
Many British hospitals were forced to divert or even cancel non-emergency procedures, and officials reported email and on-screen messages demanding money in exchange for access to computer files.
But the NHS was far from the only agency affected. The ransomware attack disrupted business at organizations and agencies across the world, CNN reported.
The malicious code called “WannaCry” locks down computer systems, forcing users to wire cash payments to receive a code to unlock systems, authorities said Friday.
“Affected machines have six hours to pay up and every few hours the ransom goes up,” Kurt Baumgartner, the principal security researcher at Kaspersky Lab, told CNN. “Most folks that have paid up appear to have paid the initial $300 in the first few hours.”
Along with Britain’s NHS, authorities in Spain also reported being hit by the ransomware attack.
Other countries, including Portugal, Japan, the Philippines, Turkey and Vietnam, also reported attacks, The New York Times reported on Friday.
Security experts say the attack exploits the Server Message Block (SMB) critical vulnerability that Microsoft tried to patch on March 14. “The 0day exploit, aka ETERNALBLUE, believed to be an NSA exploit tool, initially was leaked by the hacker group Shadowbrokers, prompting a patch from Microsoft,” according to Dawn Kawamoto.
Experts say that the ransomware code is a “hunter module” that spreads across the Internet seeking computer systems that are vulnerable to its attack. The best way to prevent an attack is for systems managers to be sure all the most current patches are applied to their systems.
The malware is also spread by malicious emails, so users are again advised not to open any email they are suspicious of or messages from people they do not know.
The British National Health Service issued a statement on Friday’s outage saying that “At this stage, we do not have any evidence that patient data has been accessed.”
Our statement on the reported ransomware issues: https://t.co/Pt47dvpbiR #nhscyberattack
— NHS Digital (@NHSDigital) May 12, 2017
Follow Warner Todd Huston on Twitter @warnerthuston or email the author at igcolonel@hotmail.com.
COMMENTS
Please let us know if you're having issues with commenting.