This morning’s key headlines from GenerationalDynamics.com
- China hackers collect data on hundreds of millions of Americans and Westerners
- China cracks down on Twitter
- China extends its ‘social credit score’ system to Americans and Westerners
- Steve Bannon: Chinese engineers working on American weapons systems
- Huawei chairman challenges U.S. to prove they’re a security risk
China hackers collect data on hundreds of millions of Americans and Westerners
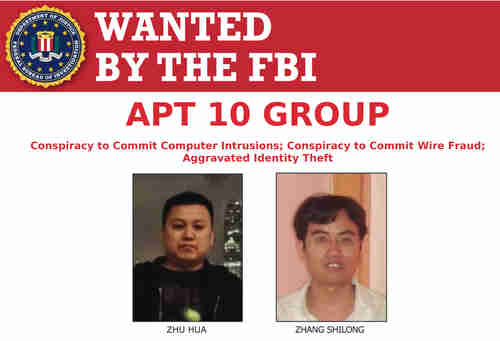
Poster showing Chinese hackers displayed at Justice Dept. press conference on Thursday
The Department of Justice on Thursday accused China of a massive international hacking scheme that penetrated commercial and military systems in at least 12 countries, including Brazil, Canada, Finland, France, Germany, India, Japan, Sweden, Switzerland, the United Arab Emirates, the United Kingdom, and the United States.
An indictment charged two Chinese nationals, Zhu Hua and Zhang Shilong, with conspiracy to commit computer intrusions, conspiracy to commit wire fraud, and aggravated identity theft.
According to the indictment:
Over the course of the Technology Theft Campaign, which began in or about 2006, Zhu, Zhang, and their coconspirators in the APT10 Group successfully obtained unauthorized access to the computers of more than 45 technology companies and U.S. Government agencies based in at least 12 states, including Arizona, California, Connecticut, Florida, Maryland, New York, Ohio, Pennsylvania, Texas, Utah, Virginia and Wisconsin. The APT10 Group stole hundreds of gigabytes of sensitive data and information from the victims’ computer systems, including from at least the following victims: seven companies involved in aviation, space and/or satellite technology; three companies involved in communications technology; three companies involved in manufacturing advanced electronic systems and/or laboratory analytical instruments; a company involved in maritime technology; a company involved in oil and gas drilling, production, and processing; and the NASA Goddard Space Center and Jet Propulsion Laboratory. In addition to those victims who had information stolen, Zhu, Zhang, and their co-conspirators successfully obtained unauthorized access to computers belonging to more than 25 other technology-related companies involved in, among other things, industrial factory automation, radar technology, oil exploration, information technology services, pharmaceutical manufacturing, and computer processor technology, as well as the U.S. Department of Energy’s Lawrence Berkeley National Laboratory.
Finally, the APT10 Group compromised more than 40 computers in order to steal sensitive data belonging to the Navy, including the names, Social Security numbers, dates of birth, salary information, personal phone numbers, and email addresses of more than 100,000 Navy personnel.
Most of the news coverage has focused on the theft of commercial and military technology and how that will be used by China’s state-run companies and military. These technologies will be useful to the Chinese as they build weapons systems and prepare to launch a war on the United States.
But for this article, I want to focus on the theft of personal data on Americans (and citizens of other Western countries).
This indictment says that a hack of navy computers stole names, Social Security numbers, dates of birth, salary information, personal phone numbers, and email addresses of more than 100,000 Navy personnel.
I recently described the Marriott hotel data breach by China’s spy agency, the Ministry of State Security (MSS) which stole names, addresses, telephone numbers, credit card numbers, passport numbers, birthdates, passport photos, hotel arrival and departure dates, and information on where people traveled and with whom on roughly 500 million guests.
Other data breaches attributed to China’s MSS include a 2017 Equifax hack that collected detailed credit information on 145 million people, a 2013 Target breach that exposed payment card and contact information for 60 million customers, and a 2015 hack of the Office of Personnel Management (OPM) that collected detailed personal information on more than 20 million government employees, family members and applicants. There were other breaches of healthcare institutions, including Anthem and CareFirst, that provided health data.
China’s military is creating a huge database of hundreds of millions of Americans. Such a database would be illegal in the United States, but it is being done by the Chinese. Dept of Justice and Dept of Justice and UK government and CNBC
China cracks down on Twitter
China’s government has complete control over databases and servers in China and can delete messages at will on Chinese social media platforms. But social media platforms outside of China, such as Twitter and Facebook, should be out of reach of the Chinese, right? In fact, since Twitter and Facebook are blocked in China, and only a person with sophisticated software skills can get to them from China, the Chinese can simply ignore them, right?
Starting in early November, China’s government launched a large campaign to remove from Twitter tweets that the government finds offensive. Many of these tweets were written years ago. Apparently, this was done very rapidly to maintain the element of surprise before Twitter users had a chance to arrange for all their tweets to be safely backed up.
If the owner of the Twitter account is in China, the government security thugs simply arrested him, brought him into a police station, and demanded that he access his Twitter account immediately and delete all his tweets. This apparently happened to quite a few people.
In many cases, however, the Chinese government was able to delete tweets from an account without the participation of the account owner, or knowing his password. The methods by which they did this are sketchy in the reports, but I believe the following is how they accomplished it.
In most online systems, you can change or reset your password automatically, and then the system sends you an e-mail message where you have to click on something to confirm the change. Only the owner of that e-mail account should have access to it, so that should provide a secure means of confirmation.
However, if your e-mail account is in China, then the Chinese government can gain control of it, and then make the password change on the Twitter account and confirm it on the e-mail account, without you even knowing.
Many online services go further and also use the telephone. Instead of (or in addition to) sending you an e-mail message, the online service will ring your telephone, using a phone number for you that it has on file, and then the recorded voice says, “press 1 to confirm or 2 to cancel,” or something like that.
In America, that should be secure means of confirmation, since only you can answer that phone number. But if it is a Chinese phone number, as in the case of e-mail, the military can take control of your phone number and then use it to confirm a password change.
There is one more method that China’s military could be using. If you have Chinese-manufactured phone from Huawei or ZTE, it is believed that these phones have back doors that the Chinese military can use to access data or even to control the phone. This would provide another method for confirming a password change.
The point is that China’s military is willing to use any means it can to steal information and they are willing to try everything, no matter how obscure, until something works. That is why they already have a database containing personal information of hundreds of millions of Americans.
Last week, I received a letter from Bowker Corp. saying that their database had been hacked, and my data might have been compromised. There are companies being hacked successfully every day, sometimes by kids in basements, sometimes by the Russians, and sometimes by the Chinese.
The Chinese, in particular, are using every technique available to them to get as much data on ordinary Americans as they can and merge it into a database that they can access at any time they want to track someone. Human Rights Watch and Radio Free Asia and Hong Kong Free Press and China Change
China extends its ‘social credit score’ system to Americans and Westerners
There has been a lot of news recently about China’s “Social Credit Score” system that has been rumored for a long time and was officially announced in December. China is creating a large “big data” database of all of its 1.3 billion people, accumulating data from a variety of departments and agencies, combining the data in individual data agency databases into a large database, and using it to create a credit score for every Chinese citizen.
The system will reward “pro-social behaviors,” such as volunteer work and blood donations. The system will penalize things like violating traffic laws or charging under-the-table fees. Agencies like tourism bodies, business regulators and transit authorities are supposed to work together. These agencies will provide data on private citizens to the central system and will then use the credit score to reward or punish citizens. In fact, the system is already partially in place in that people with unacceptable credit scores have already been blocked from booking more than 11 million flights and 4 million high-speed train trips. According to reports, other punishments include slower internet speeds, reducing access to good schools for individuals or their children, banning people from certain jobs, preventing booking at certain hotels, and losing the right to own pets.
Many Americans and Westerners view this system with little more than curiosity, thinking that applies only to Chinese citizens in China, so it does not matter to them.
Starting with Thursday’s indictments against Chinese hackers, it is becoming increasingly clear that the Chinese military is going a lot farther and creating databases of hundreds of millions of people in other countries, whether American or others. Of course, the data on foreign citizens is not readily available to the military in the way that domestic data is, but the Chinese are employing increasingly sophisticated methods to collect this data on foreign citizens, whether hacking Western commercial or government databases or using its vast population studying and working overseas to collect data and information and pass it back to China. Bloomberg and Xinhua and Independent (London) and Life Site News
Steve Bannon: Chinese engineers working on American weapons systems
China has a massive population of 1.3 billion people and considers these people to be “magic weapons” to be used in other countries to infiltrate government, military and commercial organizations, and to influence these organizations as well as to collect information about them to be sent back to China’s military.
Steve Bannon, formerly the chief strategist and advisor to President Donald Trump, has researched the extent that Chinese engineers are working on American weapons systems.
According to Bannon, many Chinese workers start out as students in American colleges, through Confucius Institutes, controlled by the Chinese Communist Party (CCP) through Beijing’s international coercive propaganda agency, the United Front Work Department (UFWD), and funded by China’s military. Every aspect of the Confucian Institutes is tightly controlled by the CCP. Teachers and teaching materials are all supplied by China. Taiwan and Tibet are portrayed as undisputed territories of China, with no alternate views permitted. The 1989 Tiananmen Square massacre, the one million Uighurs in re-education camps, the human rights abuses in China are all forbidden subjects.
Bannon says that Chinese students study in colleges to get access to the latest scientific research to be passed back to the CCP. These students become contractors to get access to the latest American weapons systems, once again for the CCP. According to Bannon, Defense Department reports on the infiltration of China into our research universities and our weapons labs show extensive infiltration:
I don’t think people understand these reports. These reports are essentially declassified reports that showed that the 300,000 students are here on student visas and the 10,000 contractors that we have the weapons labs – I think that up to 2/3 of them could be intelligence assets, intelligence officers or agents.
This is political correctness and greed and avarice writ large. How did contractors – and let’s call them out – Booz Allen and all these contractors – how do these contractors and these big government programs get so many Chinese nationals working into our weapons labs? Our weapons labs are at the cutting edge of national security. How did it happen?
…
The political correctness of it all – the Financial Times of London leaked the other day that my colleague, Stephen Miller, who’s a terrific young man, actually had the plan in place to get all 300,000 Chinese students out of the country with a way to cut the visas off right away. Not that we we’re going to execute on it, but it was even in thinking.
And obviously, it got leaked. In the Times, it goes around the State Department, et cetera. Look at all the appeasers. I am so glad. I take great pride that someone like Susan Thornton now owns a farm up in Maine because she was part of this kind of rational accommodationist, this softness in the Defense Department, in the State Department, in our intelligence services that basically went along with what China wanted to do and looked the other way.
A book titled Silent Invasion: How China Is Turning Australia into a Puppet State written by Clive Hamilton documents the extent to which Chinese nationals have infiltrated Australia’s government and influences its policies. Several publishers withdrew offers to publish the book because of pressure from the Chinese Communist Party. As one Australian commenter pointed out, he could walk into any bookstore or library in Australia and find a dozen books that accused the CIA of controlling Australia’s government and institutions, and no one would care. However, just one book about China caused a furious, threatening response from China. ( “26-Feb-18 World View — New book documents extensive Chinese infiltration into Australia’s organizations”)
The book was finally published in February, thanks to pressure from alarmed members of the Australian parliament’s national security committee. His research revealed evidence of CCP influence and infiltration in politics, culture, real estate, agriculture, universities, unions, and even primary schools. The book lists more than 40 former and sitting Australian politicians allegedly doing the work of China’s totalitarian Government, if sometimes unwittingly.
Another book documented similar infiltration into New Zealand’s government. ( “16-Feb-18 World View — Concerns grow over China’s covert infiltration into New Zealand’s government”)
There are some changes in the works. Some colleges have severed relations with Confucius Institutes and the 2019 National Defense Authorization Act, signed in August, contains provisions barring any U.S. university from using Pentagon resources for any program involving Confucius Institutes. In many cases, this will force universities to choose between receiving funding from the Pentagon and funding from China’s military.
The information provided by China’s “magic weapons,” the Chinese nationals working and studying in the West, can provide a great deal more information to add to the data collected by hacks of hotel databases and other sources. ZeroHedge and RealVision
Related Articles:
- University of N. Florida and Pentagon cut ties with China’s Confucius Institutes (30-Sep-2018)
- China recklessly arrests a second Canadian without justification (13-Dec-2018)
- New book documents extensive Chinese infiltration into Australia’s organizations (26-Feb-2018)
- Concerns grow over China’s covert infiltration into New Zealand’s government (16-Feb-2018)
Huawei chairman challenges U.S. to prove they’re a security risk
Several countries – including the United States, Britain, Canada, Australia, New Zealand, and Japan – have banned or are considering banning routers and other equipment from Huawei Technologies Ltd., the world’s largest global maker of network gear, because it is feared that these products contain “back doors” that allow them to be secretly accessed and controlled from China. The result is that Huawei is being shut out of supplying products for the latest 5G networks.
As I have said in the past, I have spent a part of my career as a senior software engineer developing chip-level operating system software for embedded systems, so I know exactly how any chip or any electronic device can be turned into a tool for espionage. Furthermore, I can tell you that not only is it doable, it is not even particularly difficult for someone with the right skills.
Now Ken Hu, the chairman of Huawei, is challenging America and other companies to provide evidence that Huawei products are in fact security risks. He complains that the accusations stem from “ideology and geopolitics.” He warned that excluding Huawei from fifth-generation networks in Australia and other markets would hurt consumers by raising prices and slowing innovation.
According to Hu: “There has never been any evidence that our equipment poses a security threat. …We have never accepted complaints from any government to damage the networks or business of any of our customers.”
The problem is that Huawei could develop a chipset that works exactly as described in the public specifications. The chipset could be subjected to thousands of tests and they would all work perfectly. But what Huawei could do is install a “backdoor” into the chipset. When the chip receives, say, a secret 1024-bit code, then it will execute commands sent to it by Chinese engineers. Thus, the Chinese are then in control of any devices with Huawei chips and it cannot be detected until it is too late.
Now, as everyone knows, I am a very helpful kind of guy, and I want to be helpful to Chairman Hu and tell him how he can regain the confidence of the West that his chips and devices do not contain backdoors. And I offer this advice in the spirit of peace, cooperation, and friendship between America and China.
Hu has the burden of proof backwards. He is asking America to prove there is a security risk. Actually, the burden is on him to do the opposite – prove affirmatively that there is no security risk. How does he do that? Here’s how:
- Hire teams of Western software and hardware engineers, selected by American, European, Australian, Japanese and other Western governments, to join the development teams in China developing Huawei products. These people will be hired to do real work and participate fully in all aspects of Huawei’s hardware and software development.This should not be a problem since China already sends Chinese workers to do the same things in American companies. So Ken Hu should be quite comfortable doing this.
- The Western engineers must have full 100 percent access to all software and firmware source code so that they can verify that the code contains no backdoors. In addition, they should have full access to the source code for all the Quality Assurance tests that are performed on all Huawei products. Once again, this is the same as for Chinese workers in America.
- The Western engineers must have full access to the entire release cycle so that they can reliably verify that all the executable code going into the devices is exactly the code that was compiled from the source code that they’ve already inspected.
- Of course, while they are working in China, the Western engineers should have full access to the internet so that they can communicate with the American government, and let them know immediately if they find anything suspicious. Again, this is the same as the access that Chinese workers in the West have.
This will permit Ken Hu to prove that Huawei’s products pose no security risks, and he can then ask that the bans to their use can be lifted.
I hope that Ken Hu will implement these suggestions, which have been offered in the spirit of peace, cooperation and friendship between the American and Chinese people, and because I would like to help him get the Huawei ban lifted. AP
Related Articles:
- Canada arrests the chief financial officer of China powerhouse Huawei (07-Dec-2018)
- China recklessly arrests a second Canadian without justification (13-Dec-2018)
- Arrest of Meng Wanzhou of China’s Huawei has increasingly serious implications (08-Dec-2018)
- Mike Pence’s China ‘containment’ speech signals more contentious US-China relations (26-Oct-2018)
- Xi Jinping invokes the 1840s Opium Wars to justify military action for China’s ‘rejuvenation’ (21-Mar-2018)
KEYS: Generational Dynamics, China, Marriot Hotel, Ministry of State Security, MSS, Zhu Hua, Zhang Shilong, APT10, Twitter, Facebook, Social Credit Score, Steve Bannon, Clive Hamilton, Australia, Silent Invasion, New Zealand, Huawei, Ken Hu
Permanent web link to this article
Receive daily World View columns by e-mail
COMMENTS
Please let us know if you're having issues with commenting.