TEL AVIV – The IDF foiled a honeypot network with false social media profiles of attractive young women created by the Hamas terror group and designed to dupe IDF soldiers, the third such operation in as many years.
Hundreds of soldiers had their phones compromised in the latest honeypot attempt.
(photo credit: IDF SPOKESPERSON’S UNIT)
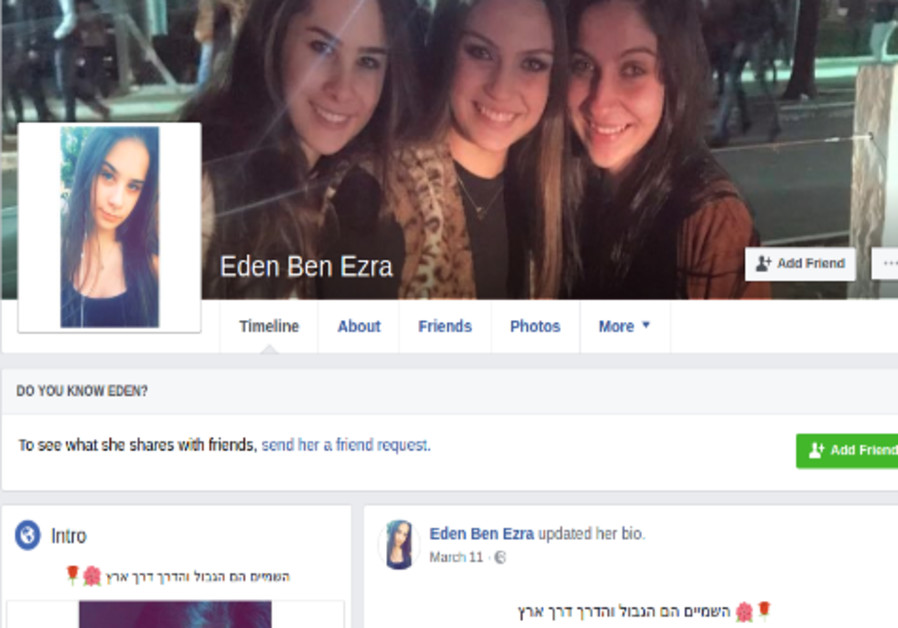
The operation consisted of six “women” posing provocatively: Sara Orlova, Maria Jacobova, Eden Ben Ezra, Noa Danon, Yael Azoulay and Rebecca Abuksis. Most of them went to some lengths to explain their poor Hebrew, either presenting themselves as new immigrants to Israel or else saying they have hearing or vision impairments.
Hamas created fake social media profiles, using photos including this one, in an attempt to hack the phones of IDF soldiers.
What Hamas didn’t know was that Israeli intelligence caught onto their plot, tracked the malware & downed Hamas’ hacking system.#CatfishCaught
— Israel Defense Forces (@IDF) February 16, 2020
The photos, which were lifted off real profiles, were doctored, the IDF said.
(photo credit: IDF SPOKESPERSON’S UNIT)
The military also said Hamas had been getting smarter about which platforms to use, extending to Telegram as well as Instagram, Facebook and WhatsApp. The terror group also sharpened its use of slang, “young” language and hashtags and in some cases even sent voice notes.
The Hamas operative, posing as a young woman, sends soldiers links to social networking apps GrixyApp, ZatuApp, Catch&See which then downloads a Trojan horse together with the app onto their phones, giving Hamas access to controls including location, contact lists, camera, and microphone.
The IDF said there had been no harm to national security. Soldiers have been called in to have the viruses removed.



COMMENTS
Please let us know if you're having issues with commenting.