This morning’s key headlines from GenerationalDynamics.com
- China’s spy chip attacks shock the computer industry
- Industry reactions to China’s spy chips
- Google is repeating the mistakes that IBM made in helping the Nazis
China’s spy chip attacks shock the computer industry
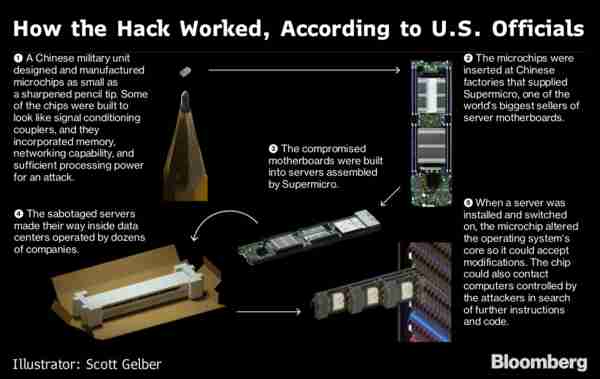
How China’s attack worked (Bloomberg)
The announcement this week by Bloomberg News that an investigation has found that China is installing backdoor chips on server motherboards is making the public aware of a major security issue that will affect a wide variety of electronic products, from iPhones to televisions to automobile components.
The attack worked as follows:
- Chinese factories manufactured motherboards to be used in computer servers. If you open a desktop computer, you can see the motherboard inside – a large board covered with chips for the CPU (microprocessor), computer memory, display processing, graphics processing, disk interface, USB interface, network interface, and so forth.
- The Chinese factories added one more chip to the motherboard: a tiny chip designed by China’s military, with its own private memory, processing power, and networking. The chip was so tiny that you probably wouldn’t notice it unless you were looking for it.
- A San Jose based American company called Super Micro Computer Inc. purchased these Chinese motherboards in quantity and installed them into servers.
- Supermicro sold the infected servers to dozens of customers, who are using them in their data centers. There are at least 30 companies, including Apple, Amazon, Facebook, a major bank, and government contractors listed.
- Once the server’s power is turned on, the Chinese military chip is activated and communicates with China’s military, ready to receive commands to take control of the server, or to steal data from networked databases.
Apple and Amazon initially denied they were victims of this attack, but apparently later confirmed that they were.
China’s foreign ministry denied that they would ever do such a thing, but said that they were victims of such attacks themselves.
These revelations have exposed only a tiny part of the problem, which is being described as the “supply chain problem.” These days, any electronic device contains chips and components from many sources, and those components themselves may be made up of chips from many sources. A complex electronic device might contain over 100 chips, sourced from different locations. If just one of those chips has been infected by China’s military, then the entire device could be compromised. As soon as the device is turned on, then the malware chip “calls home” to the Chinese military, which then has access to the entire device, whether it is an iPhone or a helicopter. Bloomberg and Bloomberg and Krebs on Security and Mashable
Industry reactions to China’s spy chips
For months, American intelligence agencies have been advising Americans not to do business with Chinese chip manufacturers Huawei Technologies Co. or ZTE Corp.
China goes out of its way to tempt Americans to buy their products by offering a lot of features and setting very low prices. The Chinese undoubtedly lose money on these sales, but the sales support a national effort for China to control as many American electronic devices as possible for future warfare.
As a Senior Software Development, I have developed embedded operating systems for chips, and I personally know how easy it would be for the Chinese to implement this policy. Huawei could develop a chipset that works fine during tests, but Huawei could install a “backdoor” into the chipset. When the chip receives, say, a secret 1024-bit code, then it will execute commands sent to it by China’s military. Thus, the Chinese are then in control of any devices with Huawei or ZTE chips. This is not only doable, it is easy to do. The “backdoor” could not be detected until an attack had been launched, and then it would be too late. So there has never been any doubt in my mind that China COULD do this, and if China CAN do it, then they WILL do it because they have engaged every part of the nation to prepare for war with the United States.
That is a different kind of situation than the one revealed this week. In this week’s case, the hacking was done not by “invisible” software, but by a visible but tiny piece of hardware.
SecurityWeek took a survey of reactions by security experts to the announcement of China’s spy chips, and what was remarkable is that no one was the least bit surprised.
Sanjay Beri, CEO, Netskope, said: “Chinese cyber infiltration is nothing new, as proven by ongoing recent attacks from elite Chinese institutions diligently working to gain access to assets from the west.”
Itzik Kotler, CTO and Co-Founder, SafeBreach, said: “Like many recent attacks, this is low-level, stealthy, and widespread. The combination of these three makes it especially frightening at first, and it certainly is rare to see such an attack in the wild.”
Rick Moy, Chief Marketing Officer at Acalvio said: “While there’s a lot of denial about the attacks, it’s completely plausible that China did, in fact, seed certain hardware with these backdoor chips. One can imagine the liabilities that firms would rather not take on by admitting this kind of a breach. However, it is entirely within the capabilities and mission scope of nation-state intel armies to infiltrate supply chains in this way.”
Joseph Carson, chief security scientist at Thycotic said: “We are one step away from a major cyber conflict or retaliation that could result in serious implications. This could be one of the biggest hacks in history. What is clear is that it is a government behind this cyber espionage and I believe it is compromised employees with privileged access that are acting as malicious insiders selecting specific targets so the supply chain has been victim of being compromised.”
Malcolm Harkins, Chief Security and Trust Officer, Cylance: “Unfortunately the only surprising element about this attack is that it’s taken so long to be uncovered in a report.” Security Week
Google is repeating the mistakes that IBM made in helping the Nazis
In the late 1930s, Thomas Watson, the founder of IBM Corp. had to decide whether to sell Hollerith card tabulating equipment to the German Nazis, at a time when they were persecuting Jews and even dropping bombs on London. Nominally, the equipment was to be used to count things like cars and cows, but it was obvious that it could also be used to count Jews. Watson did business with the Nazis even during the war and helped the Nazis with the Holocaust.
Now Google appears to be making the same mistake with China.
Google recently announced it would not help the Department of Defense with AI technology, even for purely defensive purposes.
At the same time, Google announced a major new Google AI research center in China. “I believe AI and its benefits have no borders,” said Dr. Fei-Fei Li, Chief Scientist at Google Cloud. Well, that’s a lie. Google’s AI technology will only be used outside the United States border, and inside China’s border.
China is preparing for war with the United States and has developed numerous weapons systems with no other purpose than to attack American cities, bases, and aircraft carriers. Google is willing to provide AI technology to China that can be used in these weapons to attack the United States but refuses to allow the U.S. to use its AI technology to defend itself from China’s weapons.
A separate issue is Google’s Dragonfly project. Google is using AI technology to develop a search engine for the Chinese government that will automatically track Chinese citizens who make unapproved searches and then report those individuals to the government. Vice President Mike Pence this week called on Google this week to stop development of Dragonfly because it would “strengthen Communist Party censorship and compromise the privacy of Chinese customers.”
Recent reports indicate that over a million Uighurs are imprisoned in re-education camps. AI software provides facial recognition capabilities that permit China to track the movements of all Uighurs in Xinjiang province (or other Chinese citizens) for arrest or persecution.
My guess is that during the 1930s it was young German-Americans who promoted selling IBM technology to the Nazis. Today, with Google located in Silicon Valley, it is probably young Chinese who are promoting selling AI technology to the Chinese military, but opposing its sale to the U.S. military. These Chinese workers will certainly come to grief for this betrayal of America. Guardian (London, 29-Mar-2002) and Atlantic (April 2001) and Task and Purpose (19-Jun) and The Verge
Related Articles:
- Trump blocks Broadcom acquisition of Qualcomm over national security (14-Mar-2018)
- Huawei scandal exposes potential ‘Cyberwar Pearl Harbor’ from China (14-Oct-2012)
- New report reveals massive cyber war attack by China’s army (20-Feb-2013)
- Major defense contractor QinetiQ hacked for years by China (06-May-2013)
- American businesses debate cyber counter-attack on China (13-Mar-2013)
- Discussion of China’s directive to ‘Get Ready for War’ (21-Jan-2013)
KEYS: Generational Dynamics, China, Super Micro Computer Inc., Apple, Amazon, Facebook, Huawei Technologies, ZTE Corp., IBM, Thomas Watson, Germany, Nazis, Google, Fei-Fei Li, Uighurs, Tibetans
Permanent web link to this article
Receive daily World View columns by e-mail

COMMENTS
Please let us know if you're having issues with commenting.